What is NOVAM Project?
Novam is a cyber-security platform that seeks to protect connected IoT devices while ensuring that they maintain connectivity, security, adaptability, and scalability through the implementation of Directed Acyclic Graph architecture. Additionally, Novam will focus on monitoring and mitigating security threats likely to face IoT devices through the utilization of distributed ledger technology (DLT), system defense techniques, and artificial intelligence (AI).

NOVAM uses distributed ledger technology and AI to automatically monitor and mitigate IoT threats from the secure boot chain, operating system, mobile application and network. NOVAM also provides auditing & regulatory compliance integration to threat monitoring and detection services to ensure system events are included on an immutable distributed ledger.
NOVAM Features:
- Health Check: The NOVAM client comes with the ability to run a health check built into the core functionality. By default, this feature automatically checks the security settings of the NOVAM node before saving the results to a fle. This fle can be uploaded to a custom CDN right away, or in the case of not being connected to the network, can be queued to be uploaded in the future.
- Automatic Remediation: Some of the vulnerabilities caught by a health check can be fxed automatically. These corrections will be carried out as soon as the vulnerability is found, as long as the node has a license token to cover the security fx and a network connection to post the transaction.
An update stating which automatic fxes were deployed will be posted to the NOVAM Network once available. This allows vendors and other analysts to note any issues that may compromise their network
NOVAM’s automatic remediation function will leverage frmware and software provided by clients, businesses and organizations to insure complete and correct updates.
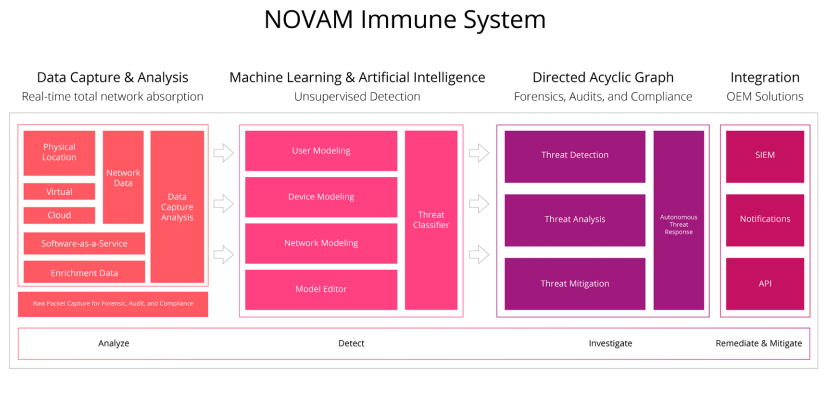
NOVAM IMMUNE SYSTEM
Rapid cyber-threat detection and attestation in an enterprise is critical to the health of the network and protection of sensitive data. Instead of pre-defning what a bad actor and malicious behavior looks like, we aim to build an embryonic, self-adaptive, model of “normal” activity and behaviors to detect and prevent against abnormalities.
Many existing security vendors have clouds where information about threats is fed in. Although optional, if all the individual systems are learning independently on the customer network, an AI should take advantage of information from other AI systems in the marketplace.
The immune system builds thorough network “vital sign” models of every user, device and network communication, ensuring total network immersion and understanding of “self”.
Using machine learning, the immune system is modeled after “self or state” of a device to establish normalized actions and pair signature-less static prevention with behavior detection. Endpoint and network activity is monitored to detect malicious behavior perpetrated by any type of threat, from advanced malware, to exploits and insider threats.
NOVAM Advantages
Distributed Ledger Technology
Novam mainly functions by utilizing DLT in order to identify, prevent, and mitigate any malicious attacks and threats to the connected IoT devices. Such threats are caused by compromised operating systems, networks, boot chains, and mobile applications.
Intuitive And Intelligent
Novam implements state-of-the –technology to assess IoT environments and provides users with ability to integrate auditing and regulatory compliance within the threat monitoring and detection services.
Transparent
Novam’s design has the capabilities of providing analytics, immutable records that can be used for auditing or in cases where the records are required for investigation purposes. This ensures transparency in all the operations carried out by Novam.
Secure
Novam will sign all messages on the platform using private keys from the Novam node. This will ensure that third parties will not be able to intercept the messages while providing a means for tracking track the origin of the message.
How Does NOVAM Work?
Novam’s system is designed to identify, alert, monitor, and initiate immune system responses and at the same time automatically mitigate, replace and quarantine potential threats. The layers of protection that Novam provides to its users ensure that all the applications on Novam are signed and verified by the health check solutions combined with trust hardware. This provides end-to-end protection since the platform will be stable and secure for applications as well as protect user’s data from malware.
NOVAM Focuses On Enterprise Networks And Devices:
Novam will protect enterprise networks and connected devices from cyber-attacks and unintended incidents. This will be through implementing DLT to provide businesses and organizations with an automated protection mechanism that features autonomous monitoring, identification, and response to threats.
Apart from providing organizations with data protection and authentication for their network, devices, and users, Novam ensures compliance with data and privacy regulations, while enabling the organization to identify compliance issues in their systems and become compliant.
Novam Tokens will be the platform’s utility tokens, as they will provide the token holders with the access to the distributed ledger capabilities and services that include monitoring, auditing, mitigation, and compliance. Furthermore, the token will decentralize the purchase of software licenses on the platform and reduce the cost associated with purchasing the licenses.
Team:


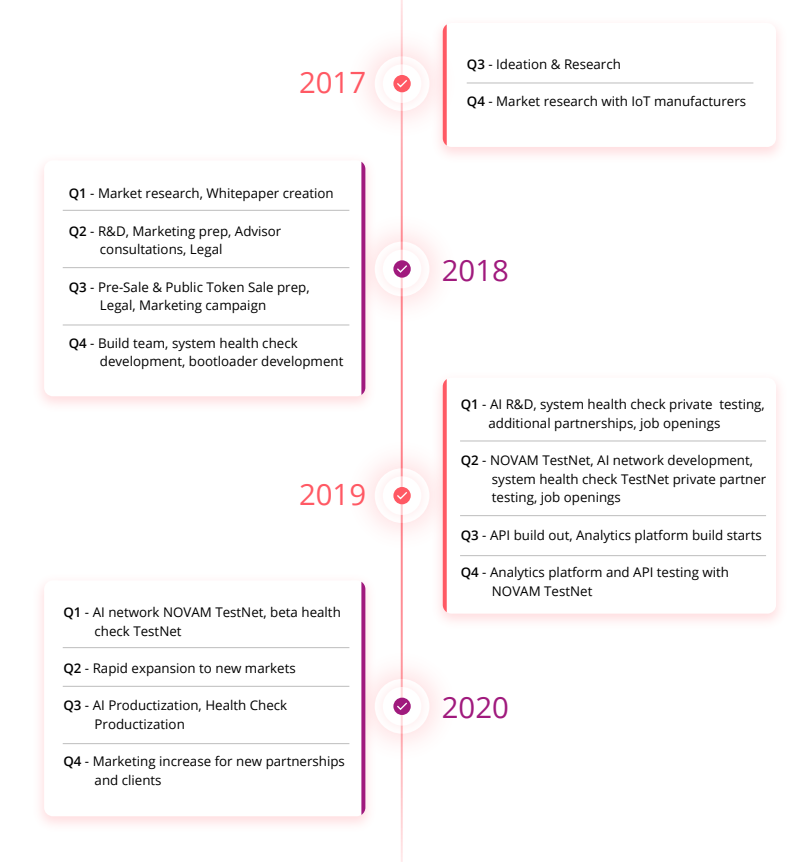
Roadmap:
Token Sales Detail:
- Token: MNVM
- Token protocol: ERC20
- Total token supply: 2,000,000,000
- Token sale date: 10 December, 2018 – 10 January, 2018
- Exchange rate: 1 MNVM = $0.06 USD
- Accepted currencies: ETH, USD
- Soft Cap: $500,000 USD
- Hard Cap: $2,076,923 USD
For more information:
Website: https://novam.ai/
Twitter: https://twitter.com/NOVAMIntl
Facebook: https://www.facebook.com/novamintl
Author: tinhkhuat
Bitcointalk Profile: https://bitcointalk.org/index.php?action=profile;u=1885373
Nhận xét
Đăng nhận xét